Operational Intelligence
Kerberos Market was architected in 2022 to address the critical stability failures of preceding darknet infrastructures. Unlike transient marketplaces, Kerberos functions as a decentralized fortress, utilizing a redundant server mesh to guarantee uptime under hostile network conditions.
Operating under the strict tenant "Be faithful to us and we will never be unfaithful to you," the platform has aggregated a verified user base exceeding 300,000 entities. With over 24,000 active cryptographic listings, Kerberos Market deploys proprietary technologies—specifically the Cataclysm Protocol and Darktrain Express—to maintain sovereignty and data integrity in an adversarial environment.
Interface Schematics
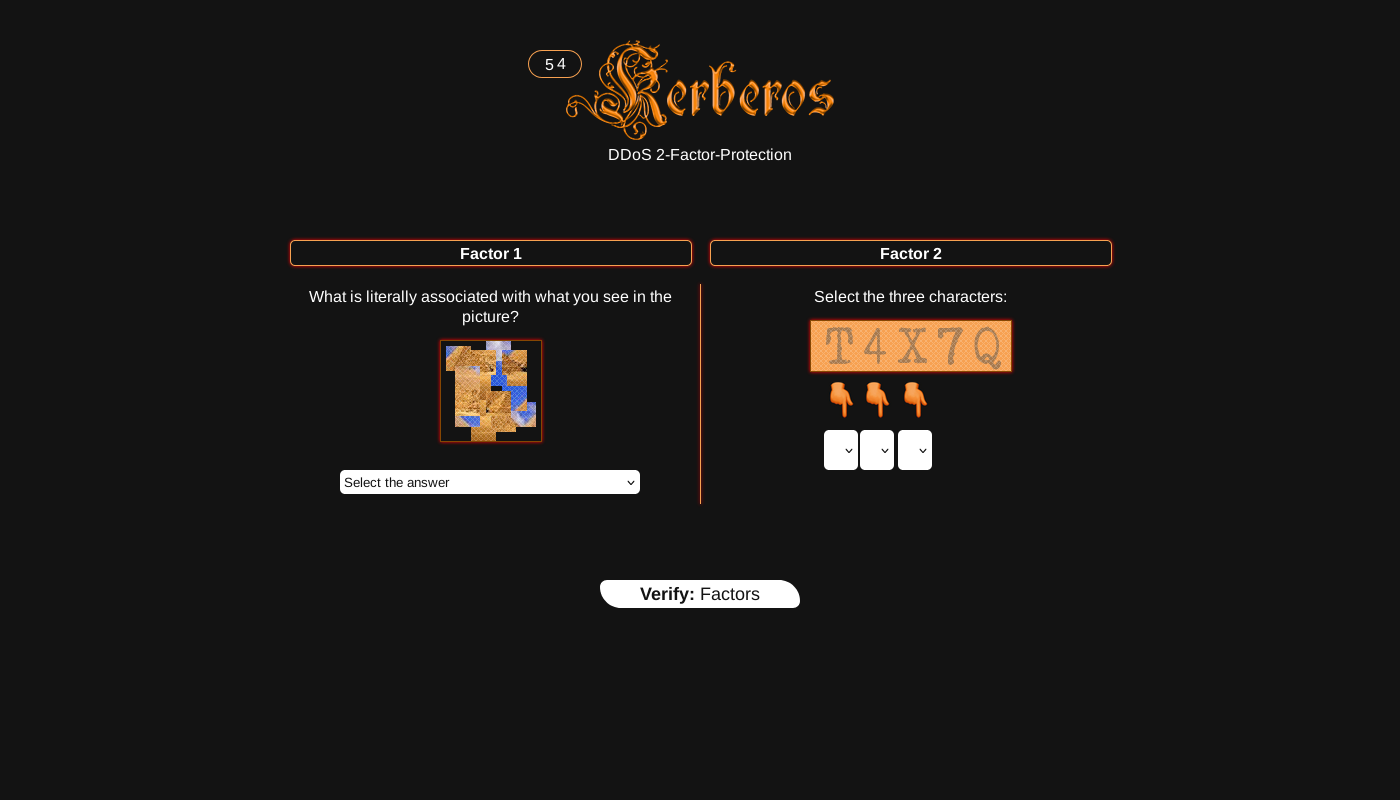
Tor Network Handshake
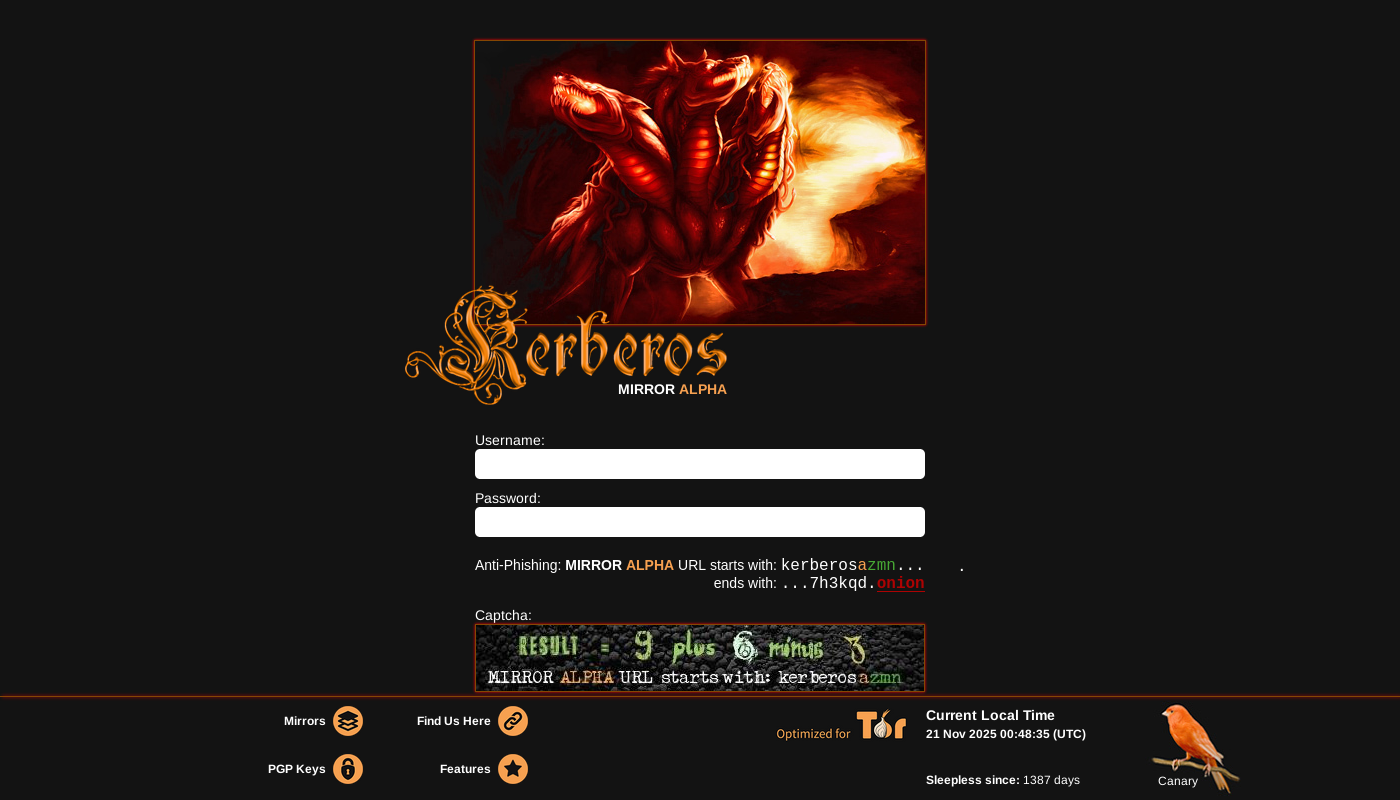
Encrypted Login Gate
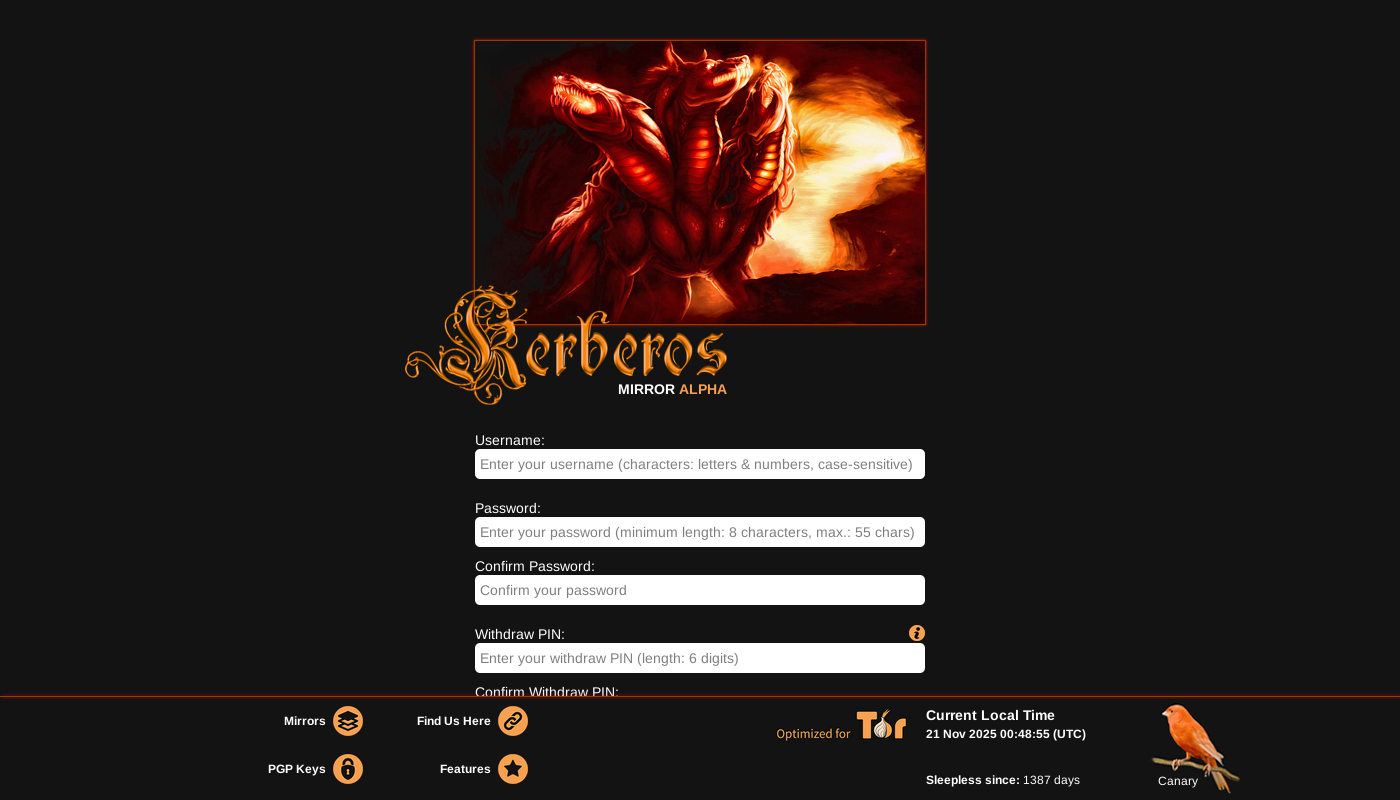
PGP Registration Protocol
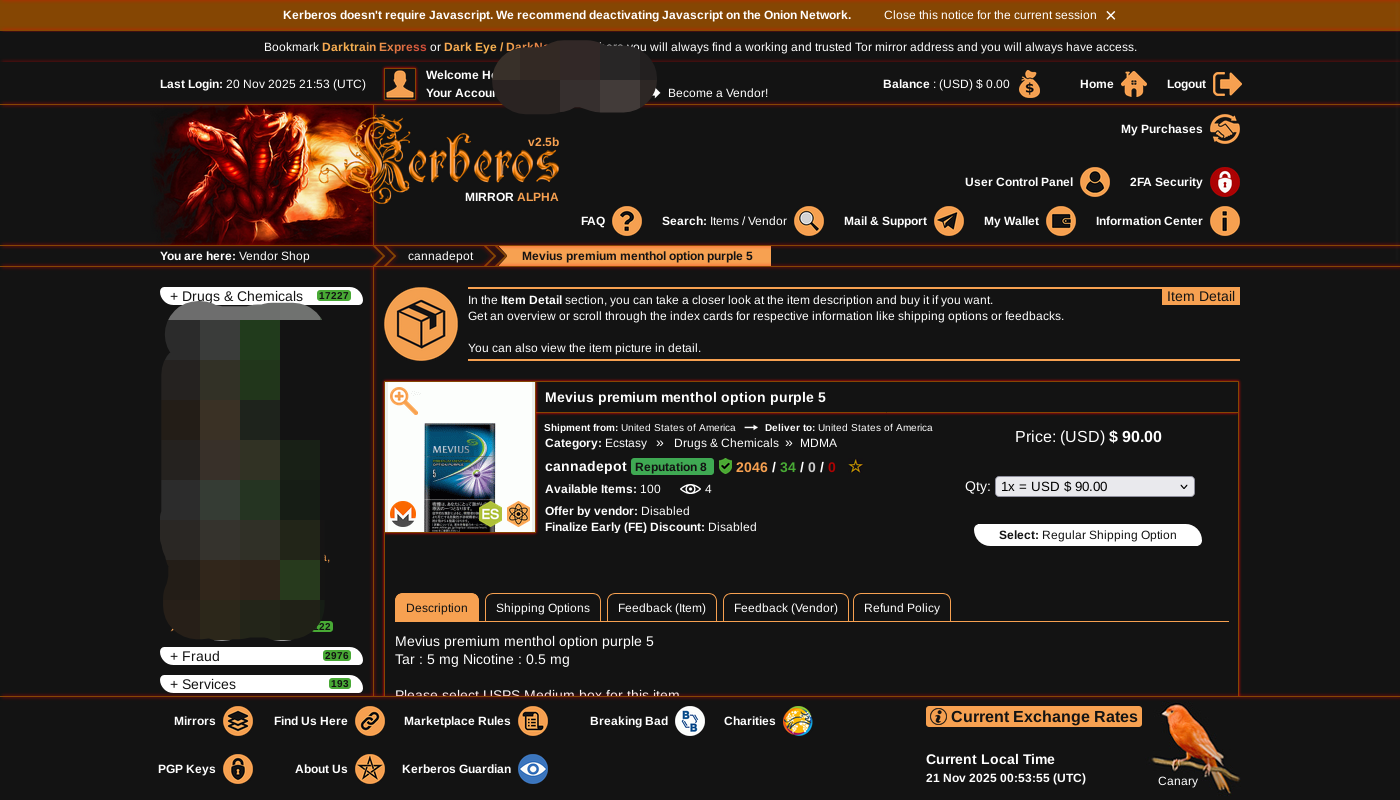
Market Mainframe
01. Cataclysm Protocol
The Cataclysm Protocol is Kerberos Market's proprietary disaster recovery framework. It ensures zero data leakage during server seizures or physical breaches by utilizing volatile RAM-disk architecture and automatic kill-switches.
- ✓ Volatile Memory Storage
- ✓ Automated Key Destruction
- ✓ Metadata Stripping
02. Darktrain Express
Darktrain Express combats network censorship and DDoS attacks through a dynamic mirror rotation system. Verified links are cryptographically signed and updated hourly to ensure consistent access routes for all users.
- ✓ Hourly Mirror Rotation
- ✓ Cryptographic Signing
- ✓ High-Bandwidth Relays
03. Economic Protocol
Kerberos Market eliminates financial friction by enforcing a strict zero-fee policy on deposits and withdrawals. Revenue is generated solely through optional vendor promotion features, ensuring maximum value retention for traders.
- ✓ 0% Deposit/Withdraw Fees
- ✓ Monero (XMR) & Bitcoin
- ✓ Integrated CoinJoin
Vendor Verification
The vendor ecosystem on Kerberos Market is curated through rigorous vetting. We host over 1,650 merchants specializing in digital goods, services, and physical assets. To maintain operational security, the platform enforces a strict "No-Logs" policy; all uploaded imagery undergoes automated stripping of EXIF data and metadata before storage.
We offer a "No Bond" transition status for verified vendors migrating from other recognized marketplaces. This lowers the barrier to entry for established entities while maintaining high trust standards via mandatory PGP video verification.
Restricted Goods
Kerberos strictly prohibits the trade of services or items that cause direct harm, including hitman services, weaponry, explosives, fentanyl/carfentanyl, poisons, and CP. Violation results in immediate termination.
Escrow & Transaction Logic
The transaction interface prioritizes speed and anonymity, defaulting to a "No-JavaScript" mode for maximum browser compatibility and security. Buyers navigate through the "Darktrain" directory or use direct search queries.
All trades are secured by multisignature escrow, requiring 2 of 3 keys (Buyer, Vendor, Market) to release funds. This system eliminates single points of failure. The standard escrow duration is 14 days, with automated dispute resolution protocols for non-complex cases, ensuring efficient fund release.
"Be faithful to us and we will never be unfaithful to you."Kerberos Administration